Putting Agents to Work: 12 predictions for the next 12 to 18 months
A strategic look at the evolution of Agentic AI over the next 18 months. We explore why tools are the new moat, why auth is the critical bottleneck, and how the shift from "chat" to "event-driven" workflows will define enterprise adoption.
On this page
- Predictions for the next 12 - 18 months
- Product Implications for Alis Ideate and Alis Build
Putting Agents to Work: 12 predictions for the next 12 to 18 months
This post is a summary of our thinking on how Agentic AI will evolve over the next 12-18 months. It started out as a memo to myself and our team to try and put some structure around the messy whipsawing technological frontier.
So here are 12 predictions for how agentic AI evolves over the next 12 to 18 months. They are grounded in what we are seeing technically, what we are hearing from operators and builders, and the pieces I keep seeing repeated across good writing in the space. I asked Gemini to critique my predictions and then tried to incorporate the pushback. The AI reviewed and critiqued (which is kind of a humbling reality to embrace), but the ideas are our own.
If you disagree, please comment. I want the feedback. And like a good Bayesian, I will update these posteriors as new data shows up.
1) Tools are the moat. Agents are the loop.
Most “agent architectures” are converging on the same core ReAct (“reason and act”) pattern: a model decides what to do next, calls a tool, reads the result, repeats. Spinning up the loop has become commoditized. Sophisticated evolutions of the ‘loop’ like Reflection / Self-Refine are quickly incorporated into frameworks like ADK for easy and rapid adoption.
The ‘work’ of applied agentic AI inside an organisation is therefore almost all about tool quality, tool safety / security, and the context those tools return.
2) Tool development shifts left, but only if the guardrails are real.
Domain experts have the context. Engineers have the implementation skill. The fastest path is usually not “make every domain expert a developer.” It will become imperative to give domain experts a golden path to express workflows, constraints, and test cases. This also means transparently removing friction from things like database management, security, infrastructure and deployment flows.
3) Tools will be a mix of crafted connectors plus MCP servers, but production requires they be remote.
Publisher MCP endpoints are great when they exist. Internal MCP wrappers will be unavoidable. Custom tools remain necessary for business logic and systems of record. The important thing: production-grade tools want to be remote, governed, and observable. Local “paste a key into your laptop” tools do not scale past the demo.
4) Workflow Builders are NOT Agents. Agents will Subsume most Workflow Builders.
Enumerating deterministic workflows by hand is painful. If AI works at all, well specified instructions plus good tools should beat clicky flowcharts for a lot of work.
But most businesses will not accept “trust me, the agent did it.” Legibility of ex post and ex ante reasoning, auditability, human-in-the-loop controls, and “dry run” modes will matter.
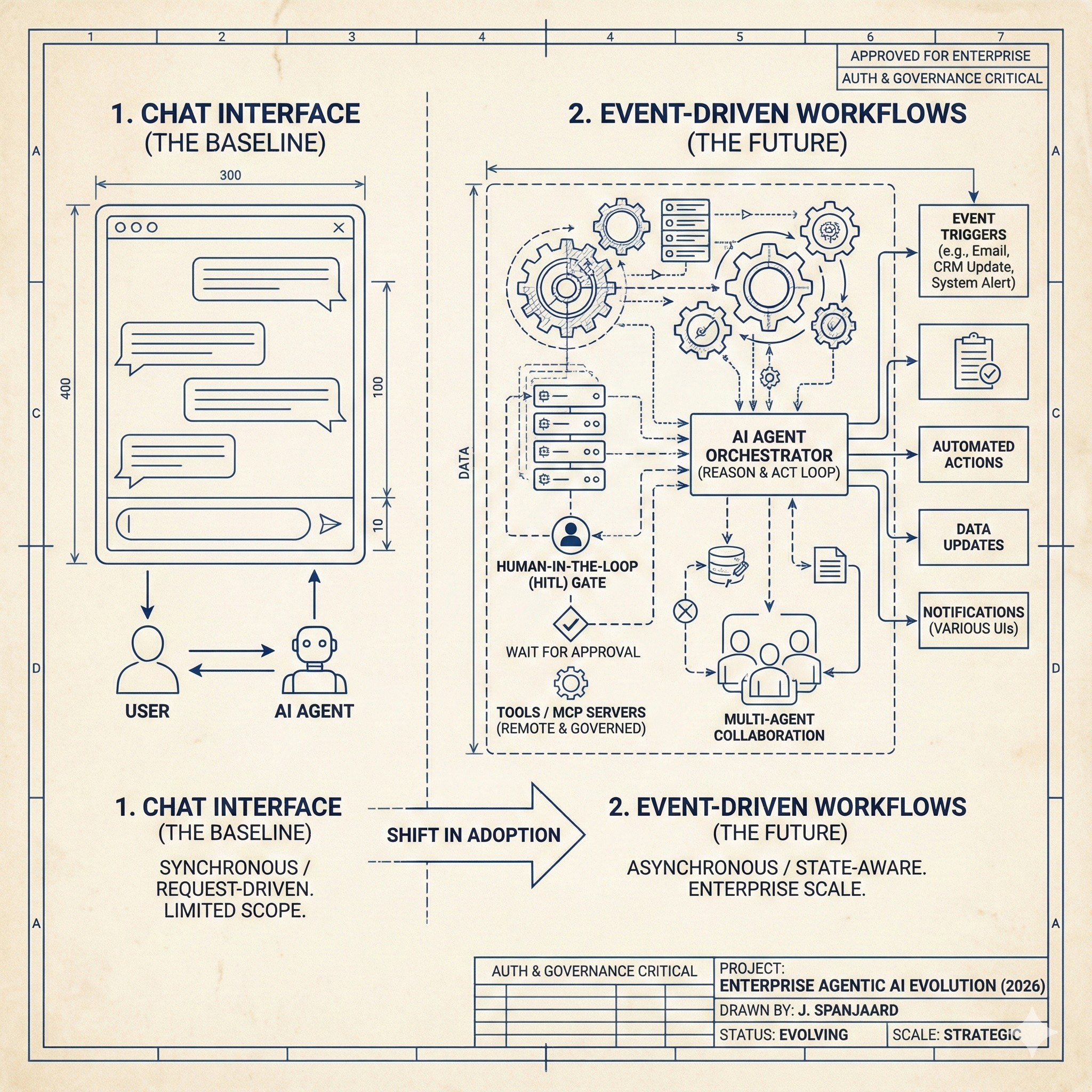
5) Agents need to go from purely user-invoked to a mixture of user and event-driven.
Today most agent work is “requested” work. You ask, it runs. The missing capability is agents reacting to state changes in your environment: email arrives, ticket created, CRM field changes, file updated.
This is where agents will start to feel like actual automation, not just a fancy chat.
6) “Waiting for Human Input” will become a more important part of SDKs and UX’s
A2A already has a HITL “Input Required” status, but the UX and “resuming session” parts of that are still clunky in many ways. The emergence of A2UI as the protocol that allows AI agents to safely send rich UIs across trust boundaries will be a key part of the puzzle for making this feel seamless.
7) The long tail kills the forward deployed engineer model
Perhaps somewhat controversially, we don’t think the FDE model scales beyond a handful of high ROI deployments. It cannot scale to the long tail of “medium value” and “niche but important” workflows inside every business. And we say that as a company that has gone from being ‘services first with internal products’ to ‘product first with a meaningful services team’.
If agentic AI is going to be ubiquitous, delivery looks more like the hyper-scaler cloud providers: some services, on-demand specialists, a rich ecosystem of partners, templates, and repeatable implementation patterns. Lots of services, but increasingly productized services supported by AI-native tools.
8) Use case discovery and ROI proof becomes the bottleneck.
The bottleneck is not “can an agent do stuff.” The bottleneck is: “Which stuff should we automate first, and how do we prove it mattered?”
Businesses are drowning in possible use cases. The winners will be the teams that can capture context, prioritise, and then measure adoption and value.
TD SYNNEX’s AI Game Plan centered around ‘discovery, scoring and activation’ provides a great example of the types of playbooks that will need to be rolled out at scale.
9) Multi-agent plus multi-UI wins. Chat is the baseline.
A2A compliant agents will be the ‘Enterprise Service Bus’ middleware of the next decade.
A lot of work is fine in chat. A lot is not. Enterprises will end up with multi-agent systems behind the scenes, and multiple UI modes in front: chat, just-in-time “GenUIs’, embedded widgets, Excel Add-ins and fully custom “AI Native” applications.
The future will look like a "low floor, high ceiling" UI strategy capitalising on the “quick wins” with out-of-the-box chat interfaces to create momentum for richer, more seamless UX experiences around that meet the user where they are at leveraging A2UI and Agent native software.
10) Dashboards get demoted.
Dashboards will remain useful for stable, shared metrics. But agents will take more of the ad hoc layer: explain, slice, generate a chart, spin up a one-off mini data app when needed. The future is less “build 50 dashboards” and more “build a few trusted metrics plus agentic access patterns.”
We continue to invest in “Reporting Exchange”, an Alis Build CodeBlock that facilitates the generation of just-in-time ‘Data Apps’ and associated artifacts (PDFs, Excel Workbooks, JSON etc.). We’re excited about the potential these have to serve as curated “data extracts” in a lot of agent workflows.
11) API-first and federated access eats away at brute force ETL
We did a decade of “copy everything into a lakehouse.” Great for analytics. Less great for action.
Agents that need to do operational work want to hit systems of record directly, with the right permissions, at the moment of action. That pushes architectures toward API-first access, and federated patterns where it makes sense. Warehouses do not go away. They just stop pretending to be the only path.
12) Everyone in this space becomes an Auth person.
The new stack is simple: UX, agent, tools. The complexity lives in access. Integrations are no longer back office plumbing. They are part of the user experience. Which means the traditional ‘non-technicals’ need to understand Auth.
From a system perspective, fine-grained authorization becomes table stakes. Per-request, resource-level checks become normal. And I think “do X as me” beats “do X for me” in many cases because it is a cleaner mental model, as long as the platform makes it safe.
I’ve noticed that the APIs of many SaaS platforms only support an “Admin Token” (as opposed to a personal access token or a proper OAuth flow and integration). In a pre-Agent world this was understandable. APIs were almost exclusively used for system-to-system integrations like “I want my spend management data to sync to my book keeping platform”. In an agent world users want to tell an agent “use this software as me” this assumption breaks down. Sure, “Browser Use” may solve for some of this, but the earliness and brittleness of Browser Use means wherever possible it's going to be “Agents calling APIs via tools”.
Alis Build treats auth as a first-class concern, providing easy patterns for "on-behalf-of" flows. There is still a lot to figure out, but we’re hard at work to make the auth golden paths easy and the guardrails safe.
Product Implications for Alis Ideate and Alis Build
In the spirit of building in public, here is how these predictions are shaping our product roadmap for Alis Ideate and Alis Build. Alis Ideate is our "AI Business Analyst" designed to help teams discover high-value use cases, uncover and consolidate tacit business context, and synthesize them into precise specifications. Alis Build is our development platform that gives engineers and semi-technical domain experts a 'golden path' to rapidly build, deploy, and govern secure, enterprise-grade agents and tools based on those specifications.
On Discovery: Alis Ideate solves the use-case discovery bottleneck by helping teams harvest use cases at scale and rigorously score them for ROI before engineering begins. We’re continuing to invest in improving the quality of generated Agent and Tool specifications. We’re also investing in features that facilitate organising, evaluating and prioritising use cases at scale.
On Shifting Left: We've put a lot of work into the core Alis Build flows to make tool initialisation, development and ‘registration’ within an agent feel accessible, fast and safe. This has meant transparently removing friction from things like database management, security, infrastructure and deployment flows.
On Remote Tools & MCP: We’re actively researching how Alis Build can better facilitate the development of secure custom MCP servers and the secure integration with published endpoints.
On Workflow Observability: We’re currently researching a light visualisation and observability layer within Alis Build called “Flows” to make it easier to capture the “stack” of tool and mult-agent calls.
On Integrations: We’re continuing to invest Alis Build CodeBlocks that are out-of-the-box integration wrappers for common systems and services with built-in caching to safely handle direct agent access to source systems.
On Auth: Alis Build treats auth as a first-class concern, providing easy patterns for "on-behalf-of" flows. There is still a lot to figure out, but we’re hard at work to make the auth golden paths easy and the guardrails safe.
Load-bearing sources
(The ones that shaped the predictions)
- Christian Posta on why MCP tooling should be remote in enterprise contexts: Blog Link
- Jamin Ball on systems of record and why action is different from analytics: Substack Link
- Fergal Reid on services-heavy B2B AI reality: Twitter Link
- Matt Slotnick on data, SaaS to AI transition, and the messy middle: Twitter Link | Substack Link
- Agentic UI protocols: AG-UI: GitHub | A2UI: Website | Agent Identity Blog


